Welcome to the FileSure Defend 2.5 Data Loss Prevention Blog series.
Data Loss Type #3: Internet-based Malware and File Compromise
The way most internet-based hacks work is by exploiting a security hole in Windows, or the browser, or another running program to run a bit of hacker-generated code. Typically what this bit of code does is to ‘infect’ the computer so the hacker can deliver a more sophisticated ‘Trojan’ virus later.
After the computer is infected, the ‘Trojan’ typically runs silently, stealing data, infecting other computers, all the while running under the infected user’s security context.
Example: If a hacker is lucky enough to infect a CFO’s computer, he will be able to exploit and steal very important data since the CFO has access to it.
Very ugly.
Who is taking data: Someone offsite, usually unconnected, and they are just grabbing whatever they can. Definitely malicious in intent.
What doesn’t (always) work: Protecting against viruses that are already known. If you happen to get a new malware infection that isn’t one of the files your virus protection is scanning for . . . you’re out of luck.
How we do it:
- Block any program from writing code to the hard drive. Period. Most people never need to write an a executable format or even a VBS file so setting up FileSure to block ALL code from being written to the drive, you stop hackers cold.
- Use a Data Loss Prevention-styled rule and block access to protected files with a ‘White-List’ of applications. Since the hacker will be using a non-authorized program, FileSure will block it from reading the file.
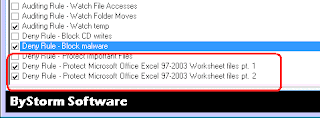
Specifically, how to do it: Here’s a screenshot showing how to define a single rule to block malware. All we do is block creating, writing or the more clever hack of renaming to program files (.exe, .dll, .vbs, .wsh) and we apply the rule to all drive types. Easy peasy . . . but note-- self-updating programs don’t like this rule so you might want to ‘Exclude’ them from the rule.
For the second half, we created an easy to use, one-page wizard to help you protect your files by limiting program access:
We run the wizard and, in this case, I decided to protect Microsoft Excel files, so I typed in ‘xls’ into the ‘Extensions’ filter and selected the entry I wanted and then clicked ‘Finish.’
This created two rules:
The first one is the ‘meat and potatoes’ rule. It blocks reading, writing and deleting of Excel files for all users anywhere—but as you see in the second screen shot, it EXCLUDES Microsoft Excel from that rule. Hence, you can only access Mircosoft Excel files IN Microsoft Excel.
With these few little characters, FileSure Defend will BLOCK all access to Excel files to every program, including malware and viruses, except for Excel, which it will allow full access.
The second rule isn’t as exciting, but does an important job. It blocks writing or creating of XLS files to removable drives and CD/DVDs for all programs (that blocks Excel from writing directly to the USB drive).
Trojan hacks are horrible since most of the time, you don’t know they are there and they are stealing data using YOUR security privileges. By using FileSure, you can be safe from them. Just too bad we haven’t figured out how to ‘Reverse hack’ them.







No comments:
Post a Comment