Data Loss Type #4: Data Loss via CD/DVD Burning
While the most popular and easiest way to steal data is to use a USB drive, another method is to burn a CD/DVD. Again, this might be intentional theft, or it might be good intentions gone wrong . . .
Example: It might seem extremely handy to a traveling sales rep to burn his client list to CD so he can read it at the hotel computer. And then forget it in the hotel computer.
Who is taking the data: Most likely an authorized user.
What doesn’t (always) work: Like USB drives, CD burning can be turned off via Windows Group Policy. However, you may not use Windows Group Policy, or you might be worried about data theft by users who aren’t normally restricted by Group Policy (e.g. Administrators). You also might want users to be able to burn some content to CD—just not the sensitive stuff. For all those scenarios, you’ll need FileSure Defend.
How we do it: In most situations, just defining a FileSure rule to block file creates on the CD/DVD drive will be enough. For maximum security, designating what programs can access your sensitive files will also be necessary.
Specifically, how to do it: Here is a screenshot showing how to set up a rule to block writing of Excel files to a CD/DVD.
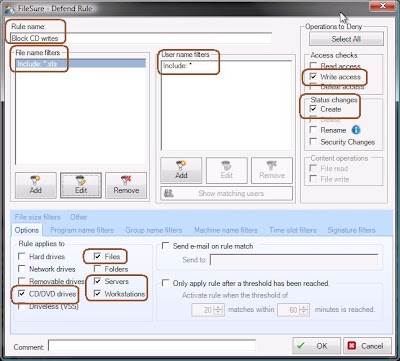
Here what we’ve done:
- Set the rule name to ‘Block CD writes’ for sanity’s sake
- Defined that the rule only apply to files with an ‘xls’ extension (‘*.xls’)
- Defined that the rule apply to all users (‘*’)
- The rule will apply to files trying to be written or created on CD/DVDs on both servers and workstations
This simple rule will probably handle 95% of theft via CD/DVDs (customized for whatever file types concern you); however, CD/DVDs are a bit different than USB drives since there isn’t a ‘file system’ on the CD/DVD until after it’s burned. So if the user was to burn a CD with another program (e.g. Nero), that writes the entire CD at once, FileSure isn’t going to catch it.
To block that scenario, it would be tempting to use FileSure’s ‘Program Name’ filter to block the CD/DVD burning program explicitly (which will work), but I like to recommend that you opt for a ‘white-list’ approach instead of a ‘black-list,’ in other words . . . exclude ALL programs from reading the protected files EXCEPT the one that is allowed to.
You can use the “Stop File Theft” wizard to achieve this very quickly, please see the previous blog Internet-based Malware and File Compromise for step by step instructions. This one-page wizard will help you designate the programs that are exclusively allowed access, and then will also generate a rule stopping writes to removable drives, so you can do it all in one place.