Data Loss Type #4: Data Loss via e-mail
E-mail is probably the most useful informational tool in the business world. Nearly every employee has an email address and many have more than one.
One of the many handy features of e-mail is attachments. Status reports, marketing presentations, sales proposals, everything gets attached to an e-mail and sent. Most of the time, all this information flying around is just fine and the only time we are exposed to any risk is when sensitive or confidential data is either intentional or inadvertently sent outside the company.
The real risk comes into play with webmail (gmail, hotmail, yahoo, and about a billion others) being used to send company files. Maybe the user just wants to work at home and doesn’t want to deal with the ‘Corporate email policy’ or maybe he is thinking of leaving the company and would like to take the ‘customer list’ for his new job.
So how can FileSure help?
How to use FileSure depends on your level of concern. Since many customers don’t want to limit use of such a powerful tool as e-mail, they use FileSure to audit their important data and setup the pre-configured report ‘Files possibly sent with webmail’ to be delivered to them every few days. Others take the extra step of setting up an alert when a browser opens a sensitive file (this indicates a file is being attached/sent via webmail, etc). We have one customer who expanded the report to include Microsoft Outlook too.
If you want to prevent files from being sent at all via webmail, we recommend that you use FileSure Defend and set up a “white list” of allowed programs. All programs will be denied access to the sensitive files, except the few you have chosen. If only Excel can open Excel files, for example, then the intermediary programs needed to attach & send webmail can’t do it. That way, if a clever user decides to ‘zip’ the customer list and then e-mail it, FileSure will catch it—and you will catch the user.
Wednesday, December 8, 2010
Wednesday, November 10, 2010
Data Loss via CD/DVD Burning
Data Loss Type #4: Data Loss via CD/DVD Burning
While the most popular and easiest way to steal data is to use a USB drive, another method is to burn a CD/DVD. Again, this might be intentional theft, or it might be good intentions gone wrong . . .
Example: It might seem extremely handy to a traveling sales rep to burn his client list to CD so he can read it at the hotel computer. And then forget it in the hotel computer.
Who is taking the data: Most likely an authorized user.
What doesn’t (always) work: Like USB drives, CD burning can be turned off via Windows Group Policy. However, you may not use Windows Group Policy, or you might be worried about data theft by users who aren’t normally restricted by Group Policy (e.g. Administrators). You also might want users to be able to burn some content to CD—just not the sensitive stuff. For all those scenarios, you’ll need FileSure Defend.
How we do it: In most situations, just defining a FileSure rule to block file creates on the CD/DVD drive will be enough. For maximum security, designating what programs can access your sensitive files will also be necessary.
Specifically, how to do it: Here is a screenshot showing how to set up a rule to block writing of Excel files to a CD/DVD.
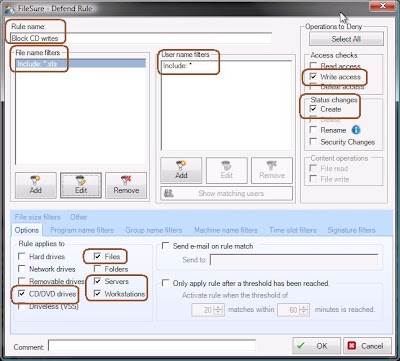
Here what we’ve done:
- Set the rule name to ‘Block CD writes’ for sanity’s sake
- Defined that the rule only apply to files with an ‘xls’ extension (‘*.xls’)
- Defined that the rule apply to all users (‘*’)
- The rule will apply to files trying to be written or created on CD/DVDs on both servers and workstations
This simple rule will probably handle 95% of theft via CD/DVDs (customized for whatever file types concern you); however, CD/DVDs are a bit different than USB drives since there isn’t a ‘file system’ on the CD/DVD until after it’s burned. So if the user was to burn a CD with another program (e.g. Nero), that writes the entire CD at once, FileSure isn’t going to catch it.
To block that scenario, it would be tempting to use FileSure’s ‘Program Name’ filter to block the CD/DVD burning program explicitly (which will work), but I like to recommend that you opt for a ‘white-list’ approach instead of a ‘black-list,’ in other words . . . exclude ALL programs from reading the protected files EXCEPT the one that is allowed to.
You can use the “Stop File Theft” wizard to achieve this very quickly, please see the previous blog Internet-based Malware and File Compromise for step by step instructions. This one-page wizard will help you designate the programs that are exclusively allowed access, and then will also generate a rule stopping writes to removable drives, so you can do it all in one place.
Monday, November 1, 2010
Internet-based Malware and File Compromise
Welcome to the FileSure Defend 2.5 Data Loss Prevention Blog series.
Data Loss Type #3: Internet-based Malware and File Compromise
The way most internet-based hacks work is by exploiting a security hole in Windows, or the browser, or another running program to run a bit of hacker-generated code. Typically what this bit of code does is to ‘infect’ the computer so the hacker can deliver a more sophisticated ‘Trojan’ virus later.
After the computer is infected, the ‘Trojan’ typically runs silently, stealing data, infecting other computers, all the while running under the infected user’s security context.
Example: If a hacker is lucky enough to infect a CFO’s computer, he will be able to exploit and steal very important data since the CFO has access to it.
Very ugly.
Who is taking data: Someone offsite, usually unconnected, and they are just grabbing whatever they can. Definitely malicious in intent.
What doesn’t (always) work: Protecting against viruses that are already known. If you happen to get a new malware infection that isn’t one of the files your virus protection is scanning for . . . you’re out of luck.
How we do it:
- Block any program from writing code to the hard drive. Period. Most people never need to write an a executable format or even a VBS file so setting up FileSure to block ALL code from being written to the drive, you stop hackers cold.
- Use a Data Loss Prevention-styled rule and block access to protected files with a ‘White-List’ of applications. Since the hacker will be using a non-authorized program, FileSure will block it from reading the file.
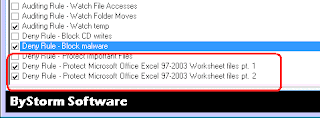
Specifically, how to do it: Here’s a screenshot showing how to define a single rule to block malware. All we do is block creating, writing or the more clever hack of renaming to program files (.exe, .dll, .vbs, .wsh) and we apply the rule to all drive types. Easy peasy . . . but note-- self-updating programs don’t like this rule so you might want to ‘Exclude’ them from the rule.
For the second half, we created an easy to use, one-page wizard to help you protect your files by limiting program access:
We run the wizard and, in this case, I decided to protect Microsoft Excel files, so I typed in ‘xls’ into the ‘Extensions’ filter and selected the entry I wanted and then clicked ‘Finish.’
This created two rules:
The first one is the ‘meat and potatoes’ rule. It blocks reading, writing and deleting of Excel files for all users anywhere—but as you see in the second screen shot, it EXCLUDES Microsoft Excel from that rule. Hence, you can only access Mircosoft Excel files IN Microsoft Excel.
With these few little characters, FileSure Defend will BLOCK all access to Excel files to every program, including malware and viruses, except for Excel, which it will allow full access.
The second rule isn’t as exciting, but does an important job. It blocks writing or creating of XLS files to removable drives and CD/DVDs for all programs (that blocks Excel from writing directly to the USB drive).
Trojan hacks are horrible since most of the time, you don’t know they are there and they are stealing data using YOUR security privileges. By using FileSure, you can be safe from them. Just too bad we haven’t figured out how to ‘Reverse hack’ them.
Thursday, October 28, 2010
USB Switchblade Malware and Data Theft
Welcome to the FileSure Defend 2.5 Data Loss Prevention Blog series.
Data Loss Type #2: USB Switchblade Malware and Data Theft
One common way for someone who has physical access to the target computers is to use a ‘USB Switchblade’ (http://www.hak5.org/w/index.php/USB_Switchblade) attack. This method uses the Windows AutoRun feature to runs a program that silently infects the computer and steals data in the by running as a background task (this same attack works with CD/DVD drives.)
Example: Recently the US Department of Defense disclosed that they were attached by a USB Switchblade attack :
Who is taking data: Since this attack is often designed with a certain computers/networks in mind, it can be custom built and will go undetected by virus scanners. This is usually a thief with an inside connection, and is a malicious removal.
What doesn’t (always) work: Some companies turn off the Autorun feature via Group Policy, and some others take a more drastic approach of disabling USB drives altogether. But in both cases, a savvy person with access to the machine can just re-enable them.
How we do it: By using FileSure Defend, you just block reading of executable code from removable drives and CD/DVDs and you’re done.
Specifically, how to do it: Here is a rule being defined in FileSure Defend, blocking reading of program files, batch files, script files, (anything that could be malicious code) from any removable drive and applying the rule to all users.
Of course, you could choose specific files, things in a certain folder, different users or groups, times of day, or more to pinpoint exactly what you are trying to accomplish with the USB write block.
Whatever choice of security you choose, FileSure records the activity, can alert on it, reports on it and archives it centrally forever in an encrypted data store.
Be sure to check out Data Loss Type #2: USB Switchblade Malware and Data Theft
Tuesday, October 26, 2010
New blog series: How FileSure Defend 2.5 handles data loss prevention.
Data Loss Type #1: File Removal via USB device
Ah, the ubiquitous USB Drive. Everything from a phone to an MP3 player can be used as a portable hard drive; all of which can be used to steal sensitive data, or introduce data you don’t want (see the #2 blog in this series for information on switchblade attacks, or keeping malicious code from being introduced via a USB device with FileSure Defend).
Example: This could be a disgruntled employee stealing trade secrets onto a pen drive, or it could be a legitimate sync of files onto a mobile device by an executive.
Who is taking data: Most likely an authorized user. Not always malicious intent: someone might want to take the sales list to work at home, not realizing the security breach that imposes.
What doesn’t (always) work: There are several solutions on the market; some options are even built right into Windows. For most people, the complete lock down of USB drives isn’t very attractive since USB drives are so useful. This opened up a space for other USB theft products, ranging from ‘Endpoint management’ products that report on what USB devices are being used to ‘White-list’ based systems where you define a list of ‘Allowed USB devices’ and some that combine both techniques. The thing is . . . it doesn’t matter what the device is, it matters what files are vulnerable.
How we do it: FileSure starts with the files. You can determine what files you don’t ever want leaving and block those from being copied TO a USB drive, period (while still leaving them otherwise available to authorized users). Or you can record or block all USB copies. You can see or block any files coming in to your environment FROM a USB drive. FileSure can also block against the powerful USB Switchblade attack where malicious data comes from the USB drive onto the computer (see the next blog entry for how to block infection via USB).
Specifically, how to do it: Here is a screenshot defining a rule that blocks the writing of Microsoft Excel files to a removable drive using FileSure Defend. All we do is block files with the extensions XLS and XLSX from being created or written to on a removable drive, and we apply it to all users.

Of course, you could choose specific files, things in a certain folder, different users or groups, times of day, or more to pinpoint exactly what you are trying to accomplish with the USB write block.
Whatever choice of security you choose, FileSure records the activity, can alert on it, reports on it and archives it centrally forever in an encrypted data store.
Be sure to check out Data Loss Type #2: USB Switchblade Malware and Data Theft
Friday, May 28, 2010
Blocking writes to DVDs
About a month ago, I was helping a customer by creating a FileSure rule to block writing to CD/DVD drives. Since the customer request occurred while I was visiting the in-laws, I used my personal laptop to define the rule.
Now, a month later, I decided to try out the Blu-Ray player on the laptop. I slapped in Planet Earth and started up WinDVD BD. spin, spin, spin….nothing. hmmm? Windows Explorer can read the disk just fine, but the WinDVD player can’t.
Reboot, reinstall WinDVD, etc… no matter what I tried, WinDVD just wouldn’t work.
Now, I’m getting serious and I start up FileSure to see there is something weird happening. As soon as I start it, the real-time monitor fills up with red lines indicating access is being denied! FileSure is blocking WinDVD access to the disk!?
Upon closer inspection, WinDVD is trying to access the DVD with WRITE access. What in the world are they thinking? Write access to play a DVD?!
Well, no matter, I turned off the block writes rule and now I’m enjoying Planet Earth is beautiful High Definition.
Now, a month later, I decided to try out the Blu-Ray player on the laptop. I slapped in Planet Earth and started up WinDVD BD. spin, spin, spin….nothing. hmmm? Windows Explorer can read the disk just fine, but the WinDVD player can’t.
Reboot, reinstall WinDVD, etc… no matter what I tried, WinDVD just wouldn’t work.
Now, I’m getting serious and I start up FileSure to see there is something weird happening. As soon as I start it, the real-time monitor fills up with red lines indicating access is being denied! FileSure is blocking WinDVD access to the disk!?
Upon closer inspection, WinDVD is trying to access the DVD with WRITE access. What in the world are they thinking? Write access to play a DVD?!
Well, no matter, I turned off the block writes rule and now I’m enjoying Planet Earth is beautiful High Definition.
Subscribe to:
Comments (Atom)